
Cybersecurity attacks are frighteningly common, and they keep recurring in new guises.
“The threat is real: studies show that 97% of successful attacks contain some form of social engineering, and over 90% begin with a phishing email. MELANI, the Swiss cybersecurity reporting center, is currently warning about fraudulent emails that appear to come from the Federal Office of Public Health, while Interpol has also warned of financial fraud associated with COVID-19.”
Palo Stacho, Head Of Operations at LUCY
But what does “phishing” mean exactly?
The term combines the words “password” and “fishing”. Phishing is a technique used to gain access to internet users’ confidential data.
Phishing is nothing new!
Internet fraudsters are exploiting the current situation by sending phishing mails that appear to contain information about COVID-19. There is no end to the creativity of phishing scammers. The first documented attempts at phishing occurred in the late 1990s. Even then, con artists used social engineering methods in attempts to get their victims to divulge confidential information so they could then use their identities. Nothing has changed when it comes to phishing except for the tools.
Cybercriminals use Trojans and other malware to worm their way into communications between senders and recipients (known as “man-in-the-middle attack”). And phishing attacks are often used to uncover access credentials such as email addresses and passwords. Fraudsters use a wide variety of techniques, including phishing emails and fake websites.
What solutions and protective measures can you implement to protect yourself against phishing attacks?
Technical solutions: using email filters, a web proxy with filter categories
Staff training: the last line of defense when cybercriminals manage to slip through the technical measures.
Cybercriminals are well aware that they can exploit human “weaknesses”, such as helpfulness or curiosity. But many phishing emails and websites are so well conceived that they are difficult to distinguish from the real thing.
How can LUCY help protect against phishing attacks?
The employees in any company are both the weakest link and the last line of defense when it comes to attacks. But if they are to be enlisted to provide their active support in combating phishing attacks, they need to be armed with the right weapons.
And the most important weapon is ongoing training with current, practical examples of cyber attacks. The company also needs the right tools to assess the effectiveness of any measures it takes.
LUCY, the IT security specialist with over 20 years’ experience in the industry, can simulate the role of a cyber attacker to help companies uncover existing vulnerabilities in their infrastructure, and to have employees identify and remedy them.
LUCY provides superb solutions:
- Attack simulations for phishing, malware, smishing (SMS phishing), USB attacks and much more besides
- Awareness training for employees with over 200 interactive, web-based training modules
- Active employee involvement in IT defense with the LUCY mail plugin for Gmail, Outlook and Office365
- Technical infrastructure tests with email and internet malware protection tests
Phishing is a dangerous way of launching cyber attacks. But we aren’t defenseless against them, because the most effective shield is trained employees!
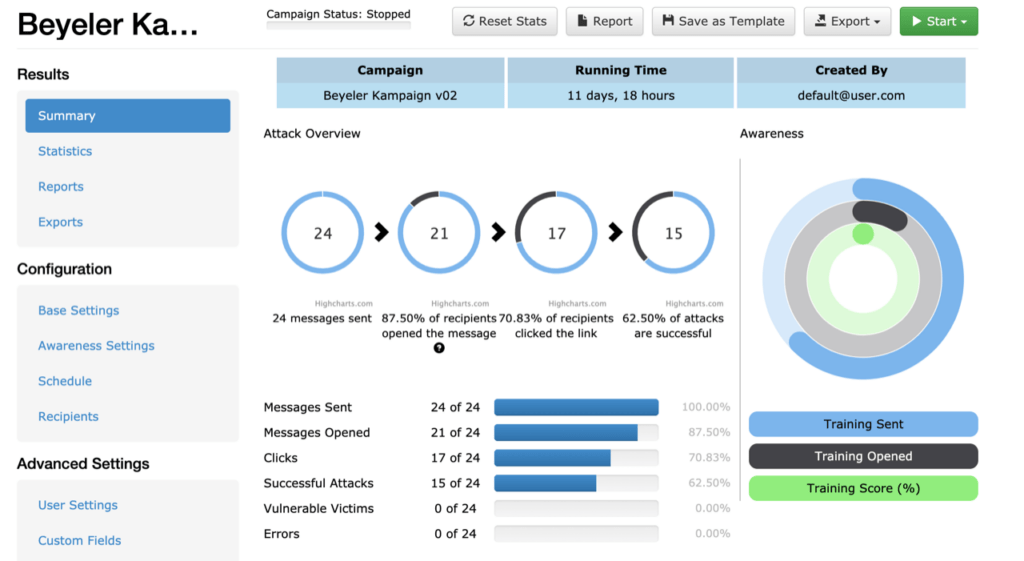
LUCY campaign cockpit with phishing simulation.
Get more information about phishing and how LUCY can protect you:
E-Mail: info@datastore.ch
